Chesa Keane, an Associate member of Global Travelers, is a long-time consultant in many aspects of IT. As members of a virtual Rotary club, we are all, by definition, on-line to various degrees. Chesa continues her excellent series on escaping internet scams, this time with a strong warning of the consequences of lax security.
For weeks we have explored how it is easy to be scammed, catfished or taken advantage of online. But in case you didn’t feel the weight of these unfortunate experiences, let’s go further to become aware of the degree to which consequences of being a victim of online (and offline) attacks may affect you.
What personal information needs to be stolen to jeopardize your life?
When you apply for a loan, think of what questions you are required to answer and what public databases are checked in the approval process for that loan. When your personal information is hijacked, it can include any or all of this provided information:
- your full name
- social security number
- birthdate
- address(es)
- employment information including salary, employer, and position
- marital status and marital partner information
- credit score

This information can and is held by the creditor often for years both offline and online. The biggest data breaches come from credit scoring agencies, credit card companies and, occasionally the bad players locally who can get this information through their job where you might have provided the info or from the credit card details you provided for a sale of the company’s product.
Worse, single bits of your personal information will lead to more information and will allow the thieves to act as you in the public world of finance. For example, they can get money for their own application using your information. Once the money is in hand, do you think they will begin making payments on that loan? No, but who will the creditor come to for that payment?
Consequences of Identify Theft
Regardless of how the breach occurred, the consequences of identity theft are extensive. Here are some of the damages with which you can expect to be coping:
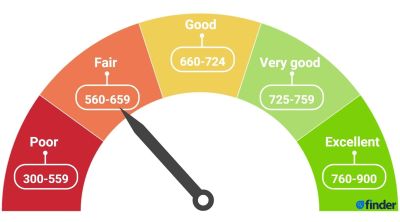
Reduction in your credit score
There are many factors which impact your credit score and if you check frequently, you will see some normal fluctuation in that score based on the percentage of outstanding debt to total credit approval amount. Ideally you should be using no more than 30% of your total approved credit. That can vary month-to-month but not usually to a great degree. Or how about those delinquencies on a loan or credit card you didn’t knowingly obtain? Thirty-five percent of your credit score is calculated on payment history and delinquencies severely affect your credit score. Imagine how misuse of your credit cards or unauthorized new loan amount can drastically decrease your credit score once someone has become YOU?

Financial hardship
If your financial accounts have been accessed, they have probably also been drained. Now how do you pay your mortgage or utility bills or groceries? Before you are aware of the now low balance in your accounts, you also might be paying bills assuming you have the money to cover your checks or online payments. When you don’t, you incur massive overdraft fees. One or two charges may be reversed by your bank occasionally, but don’t count on it when the money is gone and you have tried to pay those bills. Even so, without money to live on, you are facing some tough times.

Your financial reputation
Most organizations considering a relationship with you rely on your financial stability. Your job applications may be denied due to bad credit. Your ability to rent or purchase a home will be limited or denied. You can’t even trust that your health insurance or medical care will be available to you. Unfortunately, these damages can last for months or years.

Health insurance coverage loss
If your scammer is using your identity for medical coverage and services, you may find yourself with no ability to obtain any care at all. If you rely on specific drugs to maintain your life or to reduce your pain to a level of manageable functionality, you could be in serious trouble if someone else is claiming to be you. Some drugs are so regulated that any discrepancy threatens your ability to continue your prescriptions.

Loss of government benefits
Identity thieves can use or sell you EBT card, claim your survivor benefits, use your Medicare card for medical benefits, grab your unemployment or Social Security benefits, or stymy your ability to apply for needed government programs – now and in the future. Being slower to respond to inquiries or efforts to correct these problems, the government is even less forgiving of any abuse of your identity than many corporations. The nightmares can be endless.

Criminal charges and legal fees
Before you get this identity theft corrected, you may be faced with unexpected criminal or legal actions based on accounts that you don’t know about: tax fraud for not paying taxes incurred using your identity, debts not being paid on loans for which you didn’t apply, crimes committed using your name that you didn’t commit and more. All of which require legal representation and attorney fees can be $200/hour or more. Lawyers won’t work for free and socially based legal entities are over-burdened and often cannot provide the help you need when you need it.
There is no good news when it comes to identity theft from the actual financial burden to the emotional turmoil of potentially losing your home, your job, your protections through insurance and the vast spectrum of insecurity caused by losing you to a heartless thief.
Let’s Recap Some of the Basics You Should Absolutely Pay Attention To If you Want to Avoid Identity Theft
Previous articles in this series were designed to inform and make you aware of behaviors (or lapses) that might lead to having your identify stolen and/or your online and offline accounts accessed without your permission. Perhaps the information in this article has frightened you enough to take the time to review some of these articles (listed below). At least, review these basics:

Use strong passwords
On every online account you have, you must create strong passwords. Hint: do not use your birthdate, your children’s or partner’s birthdate, your pet’s name, or some easy to remember personal identifier. You can use passphrases or those impossible to remember long generated passwords. But I am attaching a Password Table that tells you how easy or difficult it is to break into your account depending on how complex your passwords are. Use this Password Table as a guide. Use it. No complaining about how hard it is to use strong passwords. It is less difficult than recovering your stolen identity. If your passwords are on the back of an envelope slipped under your keyboard, you might as well give up now. Get a Password Program to manage your passwords and keep it current. I have many suggestions. Just contact me.

Use two-factor authentication
It’s is useful, but difficult if you don’t manage what method you are going to use. You need to have a good phone number and email address for which you have access to from both your computers, tablets and phones. If you don’t plan this well, you can lock yourself out of your accounts and systems.

Monitor your financial accounts regularly
Financial account management is obvious, but also other non-financial unapproved access can open you to revealing too much about yourself and can lead to financial breaches as well. Treat all your accounts with care.

Beware of phishing scams
They are not always easy to spot, but if an email makes you wonder, trust that instinct. Remember that most financial institutions may notify you of a situation you may need to address, but they will not provide you a direct link from that email. Also realize that a phishing email may also give you a fake phone number. Official, real financial requests from authentic organizations will instruct you to go to your account for further measures. Go there the way you always do, not through links in the email. Phishing is difficult to identify because corporate logos and apparent emails and phone numbers are made to look real. Beware. Especially consider the message. If it appears unusual or too good to be true, it probably is.
Use secure WiFi networks to access the Internet
Going to Starbucks to deposit your paycheck online is probably not a good decision. You don’t know how secure that WiFi network is and it may open the door to accessing your accounts. In fact, the absolute rule is to do no personal work online on a public WiFi network. If you can, back up your online security with a VPN on your home or business network. Yes, this can all be inconvenient and a little annoying, but not as bad a recovering your stolen identity.

Shred personal and sensitive documents
Don’t simply toss them in a trash bag and dump them in the trash. Dumpster divers are looking for that information and who would be at fault if they found out your bank account number or credit card statements to become YOU? You can get paper shredders at Costco or an office supply store for under $100. Best investment ever.

Freeze your credit
This restricts access to your credit report which will prevent new credit card or loan applications without your knowledge. Inconvenient? It can be, but less so than all those legal fees as your try to recover your financial standing.

Get help through financial monitoring services
In my next article, I’ll provide many options for protecting your computer and your accounts. Be prepared to spend a little money, but it is not wallet-busting to be protected.
It is my hope that you feel enough pressure to protect yourself against an attack on your identification and your financial accounts to avoid careless personal identification mistakes. Let’s all be safe. You work hard for your financial security and your personal reputation. You deserve to enjoy the rewards of a life well-planned.
Looking for more? Read Chesa’s informative articles about Internet scams
- Introducing our Escaping Scams Series
- Escaping Scams #2 — Email is not always your friend
- Escaping Scams #3 — Tech Support Scam
- Escaping Scams #4 — Credit Card Reader Scams
- Escaping Scams #5 — Why We Get Scammed
- Escaping Scams #6 — If It Seems Too Good To Be True
- Escaping Scams #7 – Spoofing
- Escaping Scams #8 — The Heart Can Lie (Catfishing)
- Understanding the Internet #1 — Browser Hygiene
- Understanding the Internet #2 — What’s a VPN?

